jasonX
Bardzo aktywny
- Dołączył
- 23 Październik 2015
- Posty
- 151
- Reakcje/Polubienia
- 987
Steganos Privacy Suite 18 : A Review and Spin

Introduction
Computer security. This has been a stale discussion/debate since viruses have been spreading from all corners of the globe in this digital age.
What is your computer setup? Better yet, what is your computer security setup? Most usual answers would be his/her realtime security program such as the antivirus and firewall. Half of those who are and have been exposed to security discussions would add second-opinion antimalware applications, anti-executable/HIPS program and the like. About a fraction would state his backup solution and encryption software and the like. And the discussion goes "on and on and on...”.
But what do you use computer security for? Definitely the word "PROTECTION" or "DEFENSE" will be a resounding answer! Anyone else that would say or even state a context not related to "protection and defense" is a half-wit. Going further comes the question...what are you protecting/defending? Definitely it'll be your "system" and "data"! Both "words" intertwine in this digital age. Protecting an individual's system and data entails the user or individual's behavior and the choice of applications that will help him/her get the best protection! (I remember a linux cd from a well-known computer security software stating "Defend your data"! --yeah definitely correct there!).
There may be differences in the word "data" since (as stated) it will be on the context of the individual user. Data maybe "confidential" in nature and you would not want others to just see it without authorization. Financial information such as your credit card, social security number, bank records that could pave the way for identity theft. It may come in the form of --in the context of a group or company documents/files that contain, say, trade secrets, operational /organizational information and the like.
Some data may also be "sensitive" to you personally and may come in the form of personal secrets/information --individual privacy. You as an individual would definitely not want to lose it. To some, like me, my personal data is the most valuable thing on my system/network. It should (imho) must be the first and foremost priority to be considered protecting/defending. Why do we have such system/computer in the first place? Almost all have it to store data/information conveniently in digital form aside from their different reasons for having a computer system/gadgets. Store/retrieve data from it for whatever purpose they deem their system/gadget is for. Why should this be a first priority? Well simply put, the OS or your operating systems and applications can be reinstalled, but your data, when lost, may be irreplaceable. Sensitive data/information, even if they can be restored via backup, when exposed, may cause unrepairable damage to you or your group/company. There have been more than a handful of data leakage stories that have caused irreparable damage to their owners and entities that moving on, or even curing it, proves very difficult.
Having a layered defense/protection in your system is always best, but protecting the "files" themselves gives you more security and leverage. Yes, those "files" which contain the sensitive/confidential data. In that approach your data, whether it be confidential or sensitive, will likely to remain safe even if your layers of defense prove to be insufficient/inadequate.
There are several programs and applications (freeware/paid) that can be used for this specific purpose of protecting the files which contain your sensitive/confidential data themselves. I have been using encryption via TrueCrypt since around 2004 and relied on it for the better part of my computing years for my confidential files. Transferred to AxCrypt/AES Crypt and VeraCrypt when the TrueCrypt has been discontinued abandoned. I have been on the hunt for a suitable replacement (but not that eager to find one since I am happy with my encryption approach) and there has been a lot of applications that are touted as good replacements. One such application is Steganos Privacy Suite.
This is a review based on a "new user perspective" and trial usage of Steganos Privacy Suite 18 (SPS18) in the hope that the reader can see/understand how SPS18 can be of help to him as an individual user to protect/defend the sensitive/confidential data in his system.
So let it begin!

Steganos Privacy Suite 18 (SPS18) is a collection of tools designed for a specific purpose --to keep data you deem as "sensitive/confidential" safe from unauthorized access and exposure. The individual user will have the capability to encrypt/hide his data alongside cleaning traceable items from your browsers and system applications and permanent deletion/elimination of files/folders.
INSTALLATION
As most of the software developers and vendors now do, Steganos offers SPS18 in an online installer package which is just below (sss18int.exe) 3mb in size. You can get an offline standalone installer via request from support or its developer. It is a <59mb download (sss18intdle.exe --see end of review for official offline download link). As most applications in the market, you can try it out for 30 days without "any" restrictions to its capability/features also.
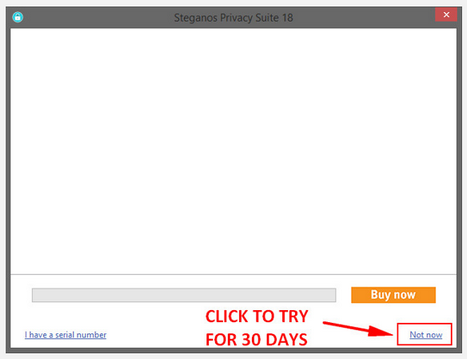
Installation of the offline package was fast and under 2 minutes and at the end of the install it will show a window where you will be asked either to buy, supply your serial number (if you have). If you want to just try it out for 30 days (without restrictions) you can just hit "Not now" and you will be taken to the user interface where you can begin your setup SPS18.
Note: If you try it out for 30 days, a pop-up (nag screen) shows everytime you start SPS18. Just click "Not now" to get to the main interface.
USER INTERFACE / COMPONENTS
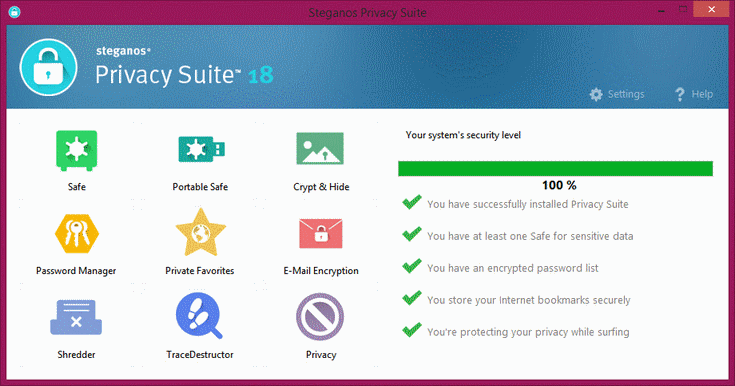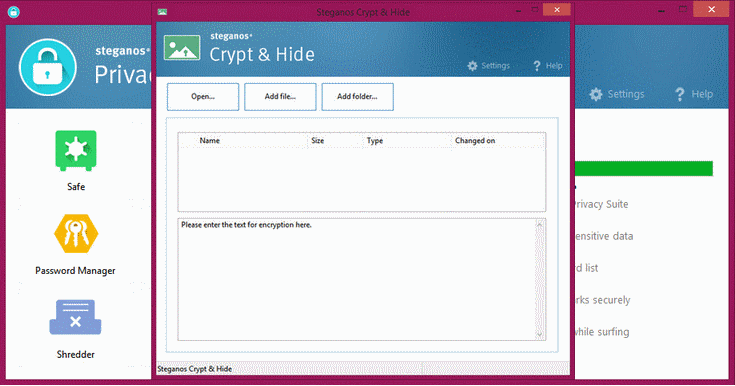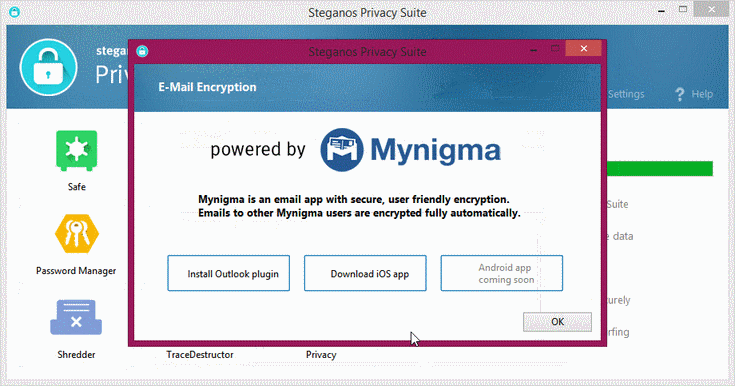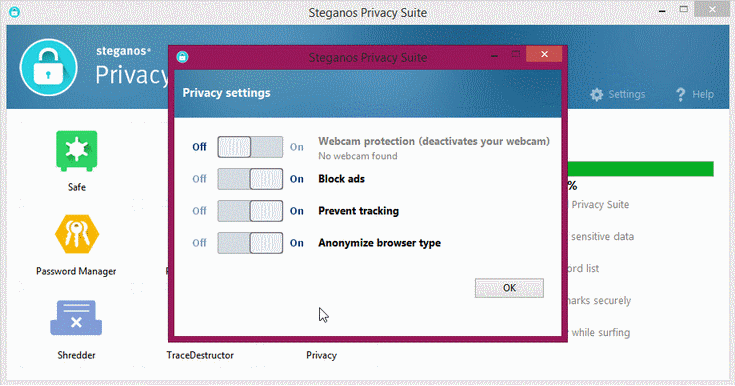
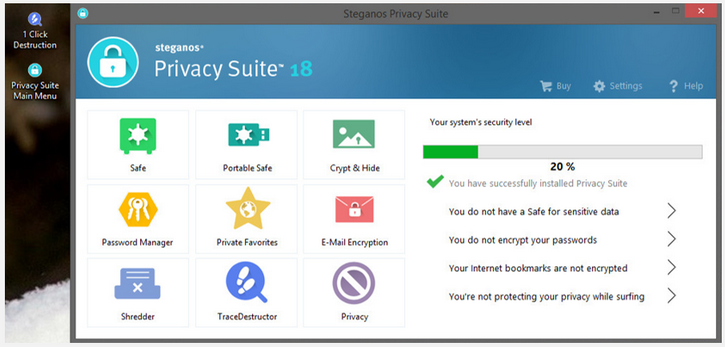
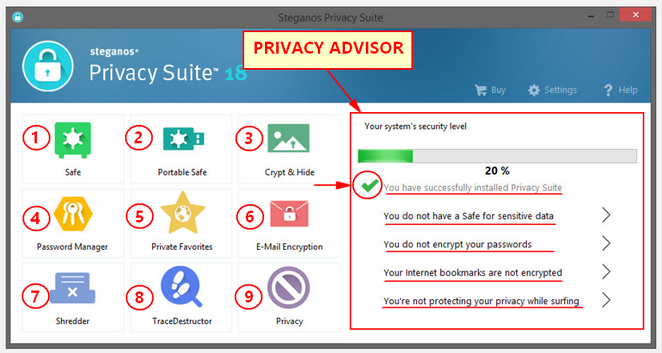
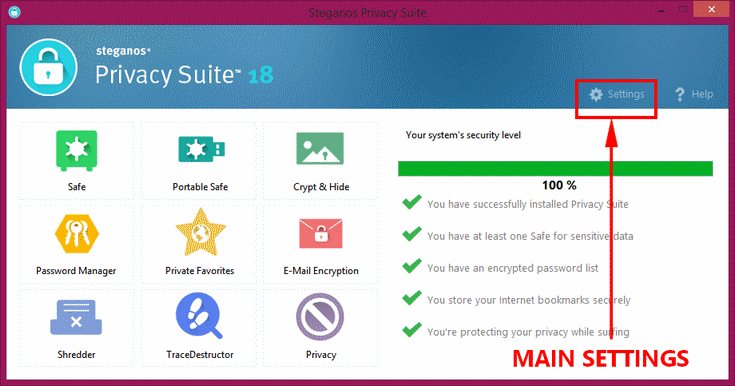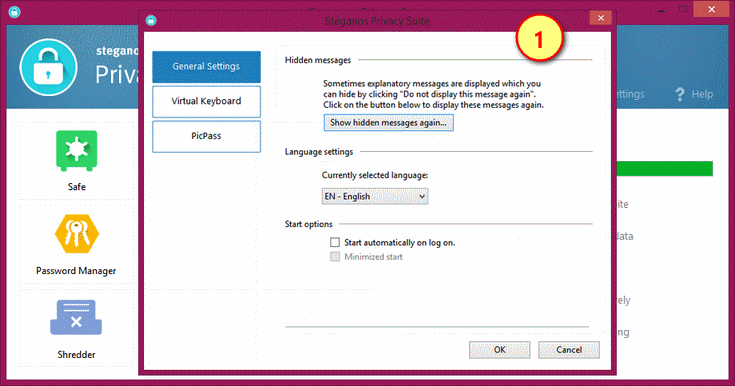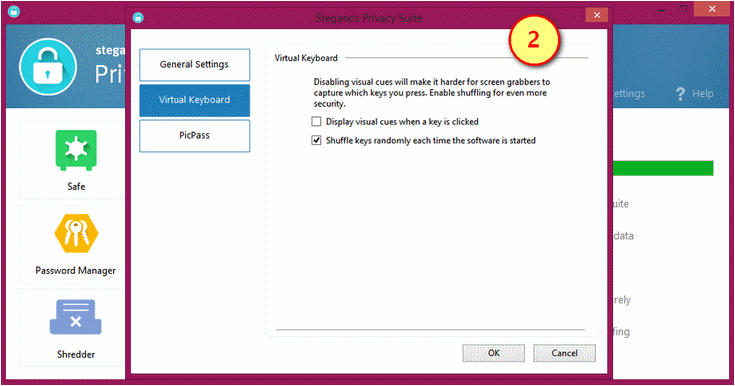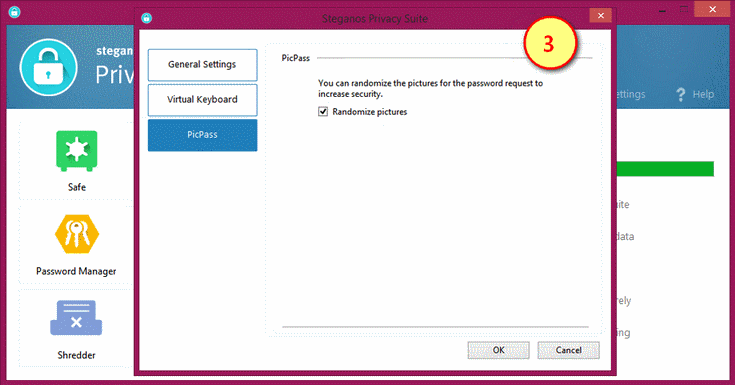
The main interface of SPS18 shows its main components which are:
1. Safe
2. Portable Safe
3. Crypt & Hide
4. Password Manager
5. Private Favorites
6. E-Mail Encryption
7. Shredder
8. TraceDestructor
9. Privacy
In the right column of the screen shows 5 categories of security level which gives you an "overview or status" of your security level as you set SSP18. A green checkmark will appear at the beginning of a category to signify that you are in fact using it. An unchecked (without a green check) category signifies that you are still not using it and from there you can click it to setup that category to further increase your security.
Click "Settings" (with the gear icon) so you can set general settings for SPS18. There are 3 options there:
1. General Settings
Settings for display or hide "Hidden Messages". Set Language settings (currently SPS18 has support for only German, English, Spanish, Portugese and French). Start options to either start SPS18 automatically on log on (with minimized start) or set it to start manually.
2. Virtual Keyboard settings
Shows two options to either (a) Display visual cues which will make it harder for screen grabbers to capture what keys you press (default), and (b) Shuffle keys randomly each time you press the keys which offers more security.
3. PicPass settings
Let's you set either to randomize the pictures for password request or not. Default setting is "randomize pictures".
1. STEGANOS SAFE
Steganos Safe is the secure drive that you will create to store your sensitive data. It is used like any other drive in your system. You can either save, edit or delete files inside your safe. To setup a Safe for your sensitive data, you can either go to (a) in the "Privacy Advisor" area click the "You do not have a Safe for sensitive data" or (b) directly go to the icon of "Safe".
Create a Safe
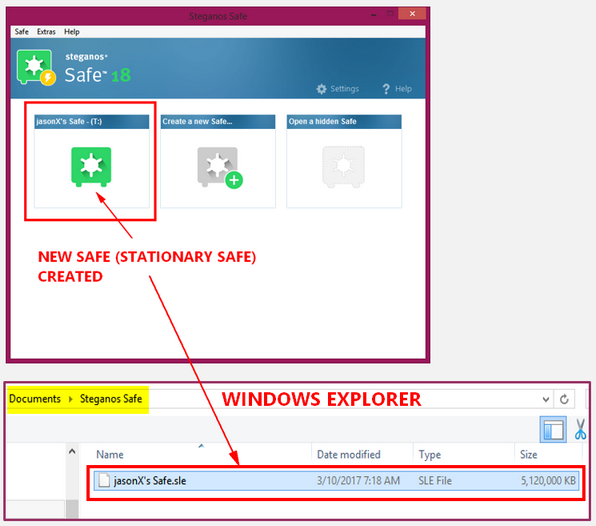
The Safe assistant (step-by-step instructions) will guide you through the creation. In the Steganos Safe window, go to the Create a new Safe> click the (+) sign there. A mini-pop-up will open where you can either select "create" or "import".
Since we are about to create our first Safe we will select "create". Note that this is a "stationary safe" and can be used only via accessing SPS18.
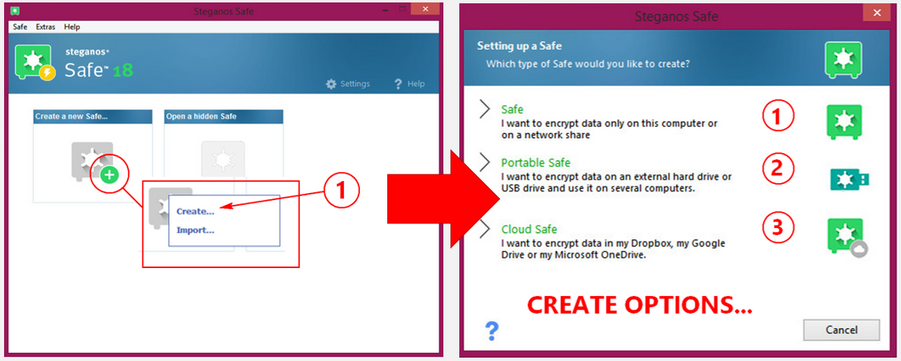
The Safe assistant shows that in the creation of a new Safe, there are 3 options given,
(1) Safe (stationary safe -- can only be accessed via the program SPS18).
(2) Portable Safe -- which by its name "portable", is a Safe that can be either in an external drive, USB or CD/DVD.
(3) Cloud Safe -- which is an encrypted Safe via Dropbox, Google Drive or MS OneDrive.
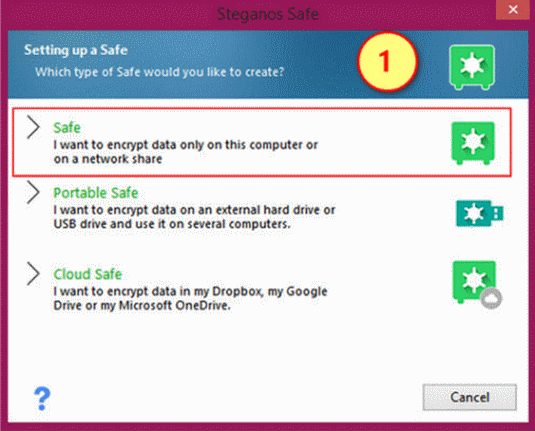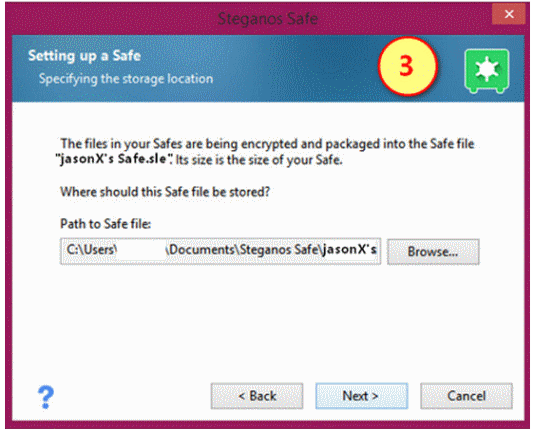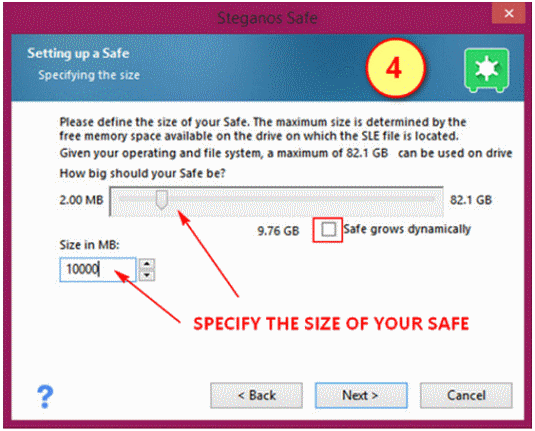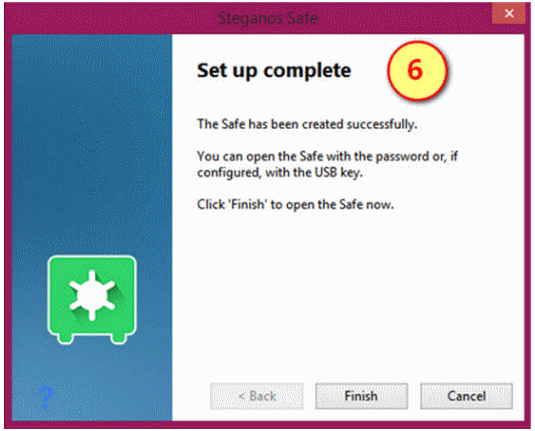
Creating a "stationary" Safe
In creating a stationary Safe, the Safe assistant (step-by-step instructions) will guide you through 6 steps.
(1) You will have to select "Safe", and
(2) Enter a name for your Safe and the drive where you want the Safe to be located in your system,
(3) Specify where the Safe file will be stored in your system --file path.
(4) Specify the size of your Safe, either by the slider provided or you can type in the "Size in MB" box. You are also given the option to set your Safe to grow dynamically as the need arises.
(5) Set a password for your Safe, either by manually entering your own password or by:
(a) Set a password via the Virtual Keyboard (type in the virtual keyboard to securely enter your password)
(b) Generate Random Password, or
(3) Use PicPass to either use a photo or symbol as password.
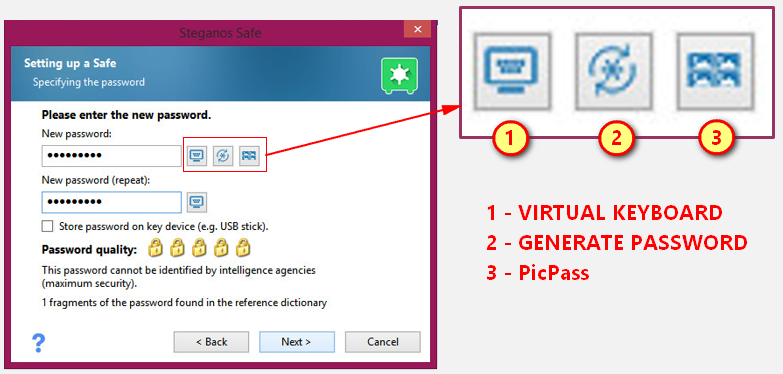
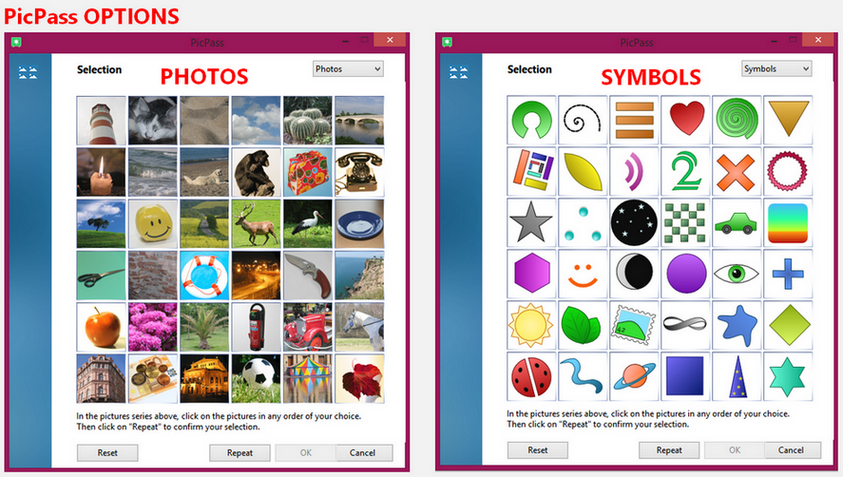
Password options
Anyone of us has in one way or another have memorized their passwords to some encrypted file or anything that require us to use a password (or in the case of ATM cards the PIN#). That is generally the most human thing to do "memorize it/remember it". But with that you are limited to securing "your password" as you will be kept in a bind so you'll make one easy to remember often. You can write it down but there also lies the problem that it isn’t secure as well as you might misplace it or lose it and their goes your password. A good password should be at least consists of 10 characters with special characters but then again the problem is there, "memorize it/remember it" or "write it down". Some use phrases which in fact will produce more than 10 characters. Some abbreviate those words in those phrases they use and insert numbers and special characters. It is really a trial and error and it is up to you to find that "balance" of creating a "secure password" which is simple to remember/memorize but is not as easy to crack (with the 10 characters with numbers/special character usage).
There are password generators that can do the job for you. This is much more secure as it is generated via random combination of characters unlike if we are the one to "generate" it on our own we tend to use words that are rather familiar to us. Through a password generator and it's usage of absolute random combination of characters a high level of security is obtained.
As seen in the previous image SPS18 offers different password options.
1) Enter/type you own password via the Virtual Keyboard.
2) Generate a random password via the password generator
3) Use PicPass which uses a combination of either "photos" or "symbols" to generate a password.
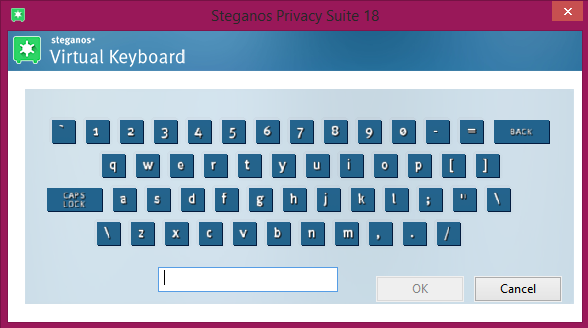
Virtual Keyboard
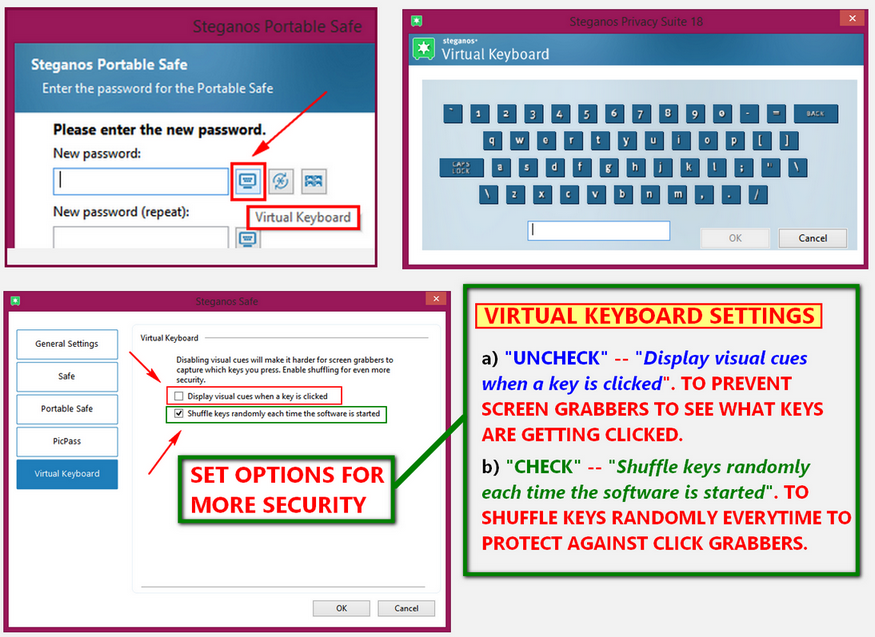
SPS18 provides its own virtual keyboard as protection for keyloggers. This the safe way of entering your password other than from your own keyboard. Please take note that to be more secure you should consider two settings:
a) "uncheck" -- Display visual cues when a key is clicked". Thus the visual movement of the virtual keyboard as you click a key will not be seen thus preventing screen-grabbers to see what keys are getting clicked.
b) "Check" -- Shuffle keys randomly each time the software is started". This provides additional protection from "click-grabbers" as the keys are shuffled (as the word implies) are randomly to no distinct location of each key is alike.
See images below.
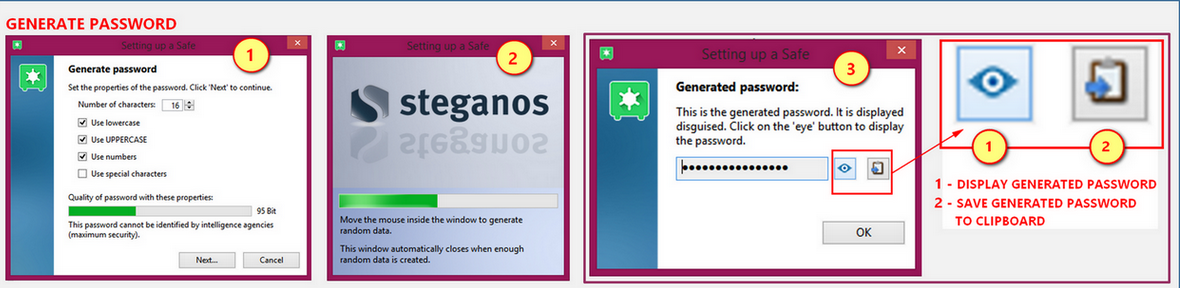
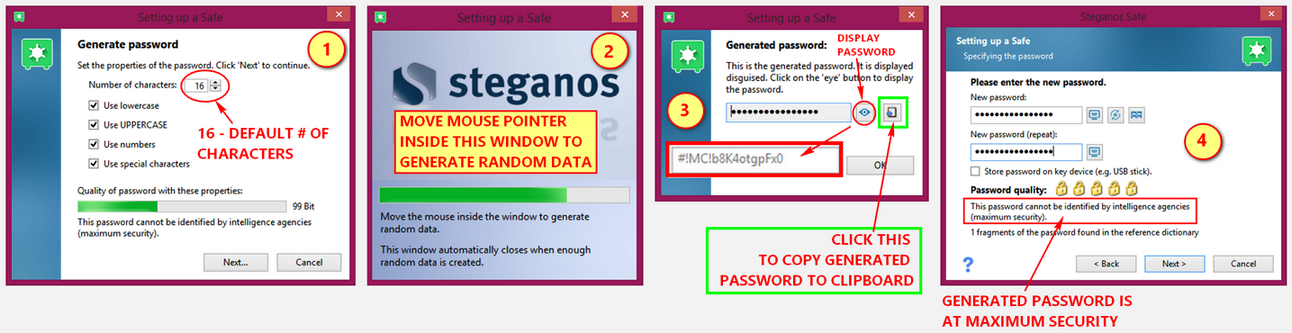
Generate random password
SPS18 default number of characters for a generated password is 16. You can however specify your own in the input field. There are checkboxes that are "checked" by default, (a) Use lowercase, (b) Use UPPERCASE, (c) Use numbers. To have a more secure password generated you can place a check-mark in "Use special characters". The quality of the password from the properties that you have set will be displayed by a "status bar". After that a window will appear instructing you to place/move the mouse pointer inside that window to generate random data. Said window will close when it is finished generating the password. As it finishes a pop-up box will show you the password generated "hidden". You can either click the "display" button so you can see it or directly copy it to clipboard. That same generated password will be automatically placed in the first field. You will have to supply the generated password in the second field (so you have to copy and paste it from the clipboard). A window will appear after you have supplied the both fields. It will also show a progress indicator complete with an explanation of how secure the generated password is. See image below.
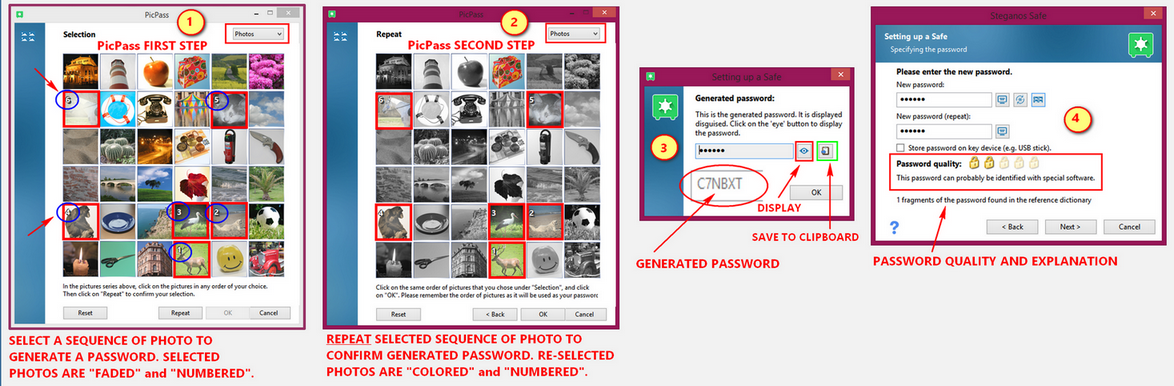
Select a password using PicPass
PicPass provides either the use of a series "photos" or "symbols" to generate a password. These picture or symbol series are to be selected or "clicked" in the order of your preference. There are two (2) sets that you need to accomplish. First set is where the "photos" or "symbols” appear colored. When you select or click a "photo" or "symbol" in the first set it will be faded and will show a number at the upper left-hand corner of the "photo" or "symbol".
Click "Repeat" button at the bottom of the window to get to the second set. You will have to repeat the sequence that you did in the first set to get a match. Think of it as the two (2) password fields in "generate random passwords". Both fields should match.
In this second set (confirmation) the "photos" or "symbols" are grayed out. As mentioned you will have to repeat the sequence that you did in the first set to get a match. As you click on to complete your sequence, the "photo" or "symbol" you select will be colored with a number at the upper left-hand corner. Click "OK" to finish. A pop-up showing your "hidden" generated password from the sequence of “photos" or "symbols" you did. Same as before the "eye" button displays the password generated and beside it, the "clipboard" button to save the generated password to clipboard.
SPS18 recommends at least 6 "photos" or "symbols" selected to form a sequence but it is advisable to combine it with special characters to highten the password quality.
See images below.
Adding files to your Safe
A Safe is a virtual drive in your system and functions as an additional HDD.
It is used like any other drive you have in your system. When a Safe is "open" a new drive is added to Windows Explorer. You can launch programs, create directories, save, edit and delete files in your Safe. You can copy/paste or drag/drop items in your Safe. When files are added to a Safe it is automatically encrypted in realtime. When "closed" your data is protected and the added "new drive" disappears in Windows Explorer.

Introduction
Computer security. This has been a stale discussion/debate since viruses have been spreading from all corners of the globe in this digital age.
What is your computer setup? Better yet, what is your computer security setup? Most usual answers would be his/her realtime security program such as the antivirus and firewall. Half of those who are and have been exposed to security discussions would add second-opinion antimalware applications, anti-executable/HIPS program and the like. About a fraction would state his backup solution and encryption software and the like. And the discussion goes "on and on and on...”.
But what do you use computer security for? Definitely the word "PROTECTION" or "DEFENSE" will be a resounding answer! Anyone else that would say or even state a context not related to "protection and defense" is a half-wit. Going further comes the question...what are you protecting/defending? Definitely it'll be your "system" and "data"! Both "words" intertwine in this digital age. Protecting an individual's system and data entails the user or individual's behavior and the choice of applications that will help him/her get the best protection! (I remember a linux cd from a well-known computer security software stating "Defend your data"! --yeah definitely correct there!).
There may be differences in the word "data" since (as stated) it will be on the context of the individual user. Data maybe "confidential" in nature and you would not want others to just see it without authorization. Financial information such as your credit card, social security number, bank records that could pave the way for identity theft. It may come in the form of --in the context of a group or company documents/files that contain, say, trade secrets, operational /organizational information and the like.
Some data may also be "sensitive" to you personally and may come in the form of personal secrets/information --individual privacy. You as an individual would definitely not want to lose it. To some, like me, my personal data is the most valuable thing on my system/network. It should (imho) must be the first and foremost priority to be considered protecting/defending. Why do we have such system/computer in the first place? Almost all have it to store data/information conveniently in digital form aside from their different reasons for having a computer system/gadgets. Store/retrieve data from it for whatever purpose they deem their system/gadget is for. Why should this be a first priority? Well simply put, the OS or your operating systems and applications can be reinstalled, but your data, when lost, may be irreplaceable. Sensitive data/information, even if they can be restored via backup, when exposed, may cause unrepairable damage to you or your group/company. There have been more than a handful of data leakage stories that have caused irreparable damage to their owners and entities that moving on, or even curing it, proves very difficult.
Having a layered defense/protection in your system is always best, but protecting the "files" themselves gives you more security and leverage. Yes, those "files" which contain the sensitive/confidential data. In that approach your data, whether it be confidential or sensitive, will likely to remain safe even if your layers of defense prove to be insufficient/inadequate.
There are several programs and applications (freeware/paid) that can be used for this specific purpose of protecting the files which contain your sensitive/confidential data themselves. I have been using encryption via TrueCrypt since around 2004 and relied on it for the better part of my computing years for my confidential files. Transferred to AxCrypt/AES Crypt and VeraCrypt when the TrueCrypt has been discontinued abandoned. I have been on the hunt for a suitable replacement (but not that eager to find one since I am happy with my encryption approach) and there has been a lot of applications that are touted as good replacements. One such application is Steganos Privacy Suite.
This is a review based on a "new user perspective" and trial usage of Steganos Privacy Suite 18 (SPS18) in the hope that the reader can see/understand how SPS18 can be of help to him as an individual user to protect/defend the sensitive/confidential data in his system.
So let it begin!
Steganos Privacy Suite 18 : A Review and Spin

Steganos Privacy Suite 18 (SPS18) is a collection of tools designed for a specific purpose --to keep data you deem as "sensitive/confidential" safe from unauthorized access and exposure. The individual user will have the capability to encrypt/hide his data alongside cleaning traceable items from your browsers and system applications and permanent deletion/elimination of files/folders.

INSTALLATION
As most of the software developers and vendors now do, Steganos offers SPS18 in an online installer package which is just below (sss18int.exe) 3mb in size. You can get an offline standalone installer via request from support or its developer. It is a <59mb download (sss18intdle.exe --see end of review for official offline download link). As most applications in the market, you can try it out for 30 days without "any" restrictions to its capability/features also.
Installation of the offline package was fast and under 2 minutes and at the end of the install it will show a window where you will be asked either to buy, supply your serial number (if you have). If you want to just try it out for 30 days (without restrictions) you can just hit "Not now" and you will be taken to the user interface where you can begin your setup SPS18.



Note: If you try it out for 30 days, a pop-up (nag screen) shows everytime you start SPS18. Just click "Not now" to get to the main interface.
USER INTERFACE / COMPONENTS
The main interface of SPS18 shows its main components which are:
1. Safe
2. Portable Safe
3. Crypt & Hide
4. Password Manager
5. Private Favorites
6. E-Mail Encryption
7. Shredder
8. TraceDestructor
9. Privacy
In the right column of the screen shows 5 categories of security level which gives you an "overview or status" of your security level as you set SSP18. A green checkmark will appear at the beginning of a category to signify that you are in fact using it. An unchecked (without a green check) category signifies that you are still not using it and from there you can click it to setup that category to further increase your security.

Click "Settings" (with the gear icon) so you can set general settings for SPS18. There are 3 options there:
1. General Settings
Settings for display or hide "Hidden Messages". Set Language settings (currently SPS18 has support for only German, English, Spanish, Portugese and French). Start options to either start SPS18 automatically on log on (with minimized start) or set it to start manually.
2. Virtual Keyboard settings
Shows two options to either (a) Display visual cues which will make it harder for screen grabbers to capture what keys you press (default), and (b) Shuffle keys randomly each time you press the keys which offers more security.
3. PicPass settings
Let's you set either to randomize the pictures for password request or not. Default setting is "randomize pictures".

1. STEGANOS SAFE
Steganos Safe is the secure drive that you will create to store your sensitive data. It is used like any other drive in your system. You can either save, edit or delete files inside your safe. To setup a Safe for your sensitive data, you can either go to (a) in the "Privacy Advisor" area click the "You do not have a Safe for sensitive data" or (b) directly go to the icon of "Safe".
Create a Safe
The Safe assistant (step-by-step instructions) will guide you through the creation. In the Steganos Safe window, go to the Create a new Safe> click the (+) sign there. A mini-pop-up will open where you can either select "create" or "import".
Since we are about to create our first Safe we will select "create". Note that this is a "stationary safe" and can be used only via accessing SPS18.

The Safe assistant shows that in the creation of a new Safe, there are 3 options given,
(1) Safe (stationary safe -- can only be accessed via the program SPS18).
(2) Portable Safe -- which by its name "portable", is a Safe that can be either in an external drive, USB or CD/DVD.
(3) Cloud Safe -- which is an encrypted Safe via Dropbox, Google Drive or MS OneDrive.

Creating a "stationary" Safe
In creating a stationary Safe, the Safe assistant (step-by-step instructions) will guide you through 6 steps.
(1) You will have to select "Safe", and
(2) Enter a name for your Safe and the drive where you want the Safe to be located in your system,
(3) Specify where the Safe file will be stored in your system --file path.
(4) Specify the size of your Safe, either by the slider provided or you can type in the "Size in MB" box. You are also given the option to set your Safe to grow dynamically as the need arises.
(5) Set a password for your Safe, either by manually entering your own password or by:
(a) Set a password via the Virtual Keyboard (type in the virtual keyboard to securely enter your password)
(b) Generate Random Password, or
(3) Use PicPass to either use a photo or symbol as password.





Password options
Anyone of us has in one way or another have memorized their passwords to some encrypted file or anything that require us to use a password (or in the case of ATM cards the PIN#). That is generally the most human thing to do "memorize it/remember it". But with that you are limited to securing "your password" as you will be kept in a bind so you'll make one easy to remember often. You can write it down but there also lies the problem that it isn’t secure as well as you might misplace it or lose it and their goes your password. A good password should be at least consists of 10 characters with special characters but then again the problem is there, "memorize it/remember it" or "write it down". Some use phrases which in fact will produce more than 10 characters. Some abbreviate those words in those phrases they use and insert numbers and special characters. It is really a trial and error and it is up to you to find that "balance" of creating a "secure password" which is simple to remember/memorize but is not as easy to crack (with the 10 characters with numbers/special character usage).
There are password generators that can do the job for you. This is much more secure as it is generated via random combination of characters unlike if we are the one to "generate" it on our own we tend to use words that are rather familiar to us. Through a password generator and it's usage of absolute random combination of characters a high level of security is obtained.
As seen in the previous image SPS18 offers different password options.
1) Enter/type you own password via the Virtual Keyboard.
2) Generate a random password via the password generator
3) Use PicPass which uses a combination of either "photos" or "symbols" to generate a password.
Virtual Keyboard
SPS18 provides its own virtual keyboard as protection for keyloggers. This the safe way of entering your password other than from your own keyboard. Please take note that to be more secure you should consider two settings:
a) "uncheck" -- Display visual cues when a key is clicked". Thus the visual movement of the virtual keyboard as you click a key will not be seen thus preventing screen-grabbers to see what keys are getting clicked.
b) "Check" -- Shuffle keys randomly each time the software is started". This provides additional protection from "click-grabbers" as the keys are shuffled (as the word implies) are randomly to no distinct location of each key is alike.
See images below.

Generate random password
SPS18 default number of characters for a generated password is 16. You can however specify your own in the input field. There are checkboxes that are "checked" by default, (a) Use lowercase, (b) Use UPPERCASE, (c) Use numbers. To have a more secure password generated you can place a check-mark in "Use special characters". The quality of the password from the properties that you have set will be displayed by a "status bar". After that a window will appear instructing you to place/move the mouse pointer inside that window to generate random data. Said window will close when it is finished generating the password. As it finishes a pop-up box will show you the password generated "hidden". You can either click the "display" button so you can see it or directly copy it to clipboard. That same generated password will be automatically placed in the first field. You will have to supply the generated password in the second field (so you have to copy and paste it from the clipboard). A window will appear after you have supplied the both fields. It will also show a progress indicator complete with an explanation of how secure the generated password is. See image below.

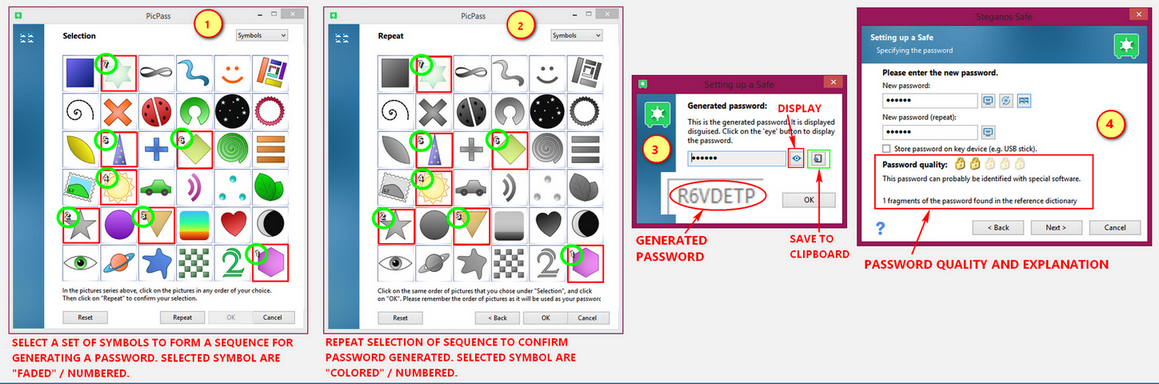
Select a password using PicPass
PicPass provides either the use of a series "photos" or "symbols" to generate a password. These picture or symbol series are to be selected or "clicked" in the order of your preference. There are two (2) sets that you need to accomplish. First set is where the "photos" or "symbols” appear colored. When you select or click a "photo" or "symbol" in the first set it will be faded and will show a number at the upper left-hand corner of the "photo" or "symbol".
Click "Repeat" button at the bottom of the window to get to the second set. You will have to repeat the sequence that you did in the first set to get a match. Think of it as the two (2) password fields in "generate random passwords". Both fields should match.
In this second set (confirmation) the "photos" or "symbols" are grayed out. As mentioned you will have to repeat the sequence that you did in the first set to get a match. As you click on to complete your sequence, the "photo" or "symbol" you select will be colored with a number at the upper left-hand corner. Click "OK" to finish. A pop-up showing your "hidden" generated password from the sequence of “photos" or "symbols" you did. Same as before the "eye" button displays the password generated and beside it, the "clipboard" button to save the generated password to clipboard.
SPS18 recommends at least 6 "photos" or "symbols" selected to form a sequence but it is advisable to combine it with special characters to highten the password quality.
See images below.


Adding files to your Safe
A Safe is a virtual drive in your system and functions as an additional HDD.
It is used like any other drive you have in your system. When a Safe is "open" a new drive is added to Windows Explorer. You can launch programs, create directories, save, edit and delete files in your Safe. You can copy/paste or drag/drop items in your Safe. When files are added to a Safe it is automatically encrypted in realtime. When "closed" your data is protected and the added "new drive" disappears in Windows Explorer.
Ostatnia edycja:
























































